Data Privacy , Data Security , Governance & Risk Management
Attackers Could Gain Control of 2 Flawed Patient Monitors
Feds Warn Flaws Could Lead to 'Simultaneous Exploitation' of All Devices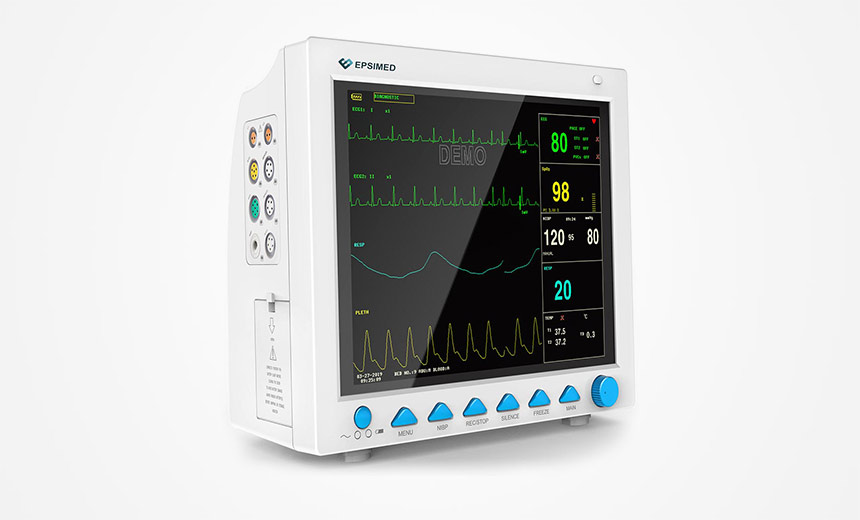
Patients are being advised to sever their health monitor's connection to the internet as U.S. federal authorities warn that cybersecurity vulnerabilities in two brands of patient monitors could allow remote attackers to take control of potentially thousands of devices all at once.
See Also: Four Imperatives Financial Institutions Face in the Digital Era
Authorities and researchers say remote attackers could manipulate the vulnerable monitors in many ways - from shutting down a device to stealing patient information. "Simultaneous exploitation of all vulnerable devices on a shared network is possible," the Cybersecurity Infrastructure and Security Agency said.
The Food and Drug Administration in an alert on Thursday said the issues concern two brands of patient monitors - Contec CMS8000 and Epsimed MN-120. The Epsimed monitors are Contec CMS8000 patient monitors relabeled as MN-120, the FDA said.
The monitors, which are used in both healthcare and home settings for displaying vital sign information such as patient temperature, heart rate and blood pressure, contain three vulnerabilities that may put patients at risk after being connected to the internet.
"These cybersecurity vulnerabilities can allow unauthorized actors to bypass cybersecurity controls, gaining access to and potentially manipulating the device," the FDA said, adding that it not aware of any cybersecurity incidents, injuries or deaths related to these cybersecurity vulnerabilities at this time.
The CISA also issued an advisory about the patient monitor vulnerabilities, which involve out-of-bounds write or CVE-2024-12248, hidden backdoor functionality or CVE-2025-0626 and privacy leakage or CVE-2025-0683.
"Successful exploitation of these vulnerabilities could allow an attacker to remotely send specially formatted UDP requests or connect to an unknown external network that would allow them to write arbitrary data, resulting in remote code execution," CISA said.
A hacker exploiting the vulnerabilities can deny access to the device, such as cause the device to crash and be unable to work as intended, and remotely perform unexpected or undesired actions, such as corrupting the data, the FDA said.
An anonymous researcher reported the vulnerabilities to CISA. No patch is currently available to address the vulnerabilities, the FDA said.
Hidden Reverse Backdoor
CISA in an additional fact sheet said that upon receiving the vulnerability report about the patient monitors from an external researcher, CISA's own research team dug in further, finding that the reverse backdoor "provides automated connectivity to a hard-coded IP address from the Contec CMS8000 devices, allowing the device to download and execute unverified remote files."*
Publicly available records show that the IP address is not associated with a medical device manufacturer or medical facility but a third-party university, CISA said. "By reviewing the firmware code, the team determined that the functionality is very unlikely to be an alternative update mechanism, exhibiting highly unusual characteristics that do not support the implementation of a traditional update feature," CISA said.
"For example, the function provides neither an integrity checking mechanism nor version tracking of updates. When the function is executed, files on the device are forcibly overwritten, preventing the end customer - such as a hospital - from maintaining awareness of what software is running on the device," CISA said. "These types of actions and the lack of critical log/auditing data go against generally accepted practices and ignore essential components for properly managed system updates, especially for medical devices."
Neither Contec nor Epsimed immediately responded to Information Security Media Group's requests for comment on the vulnerabilities.
Taking Action
The FDA recommends that patients and caregivers using the monitors at home should unplug the device's Ethernet cable and disable its wireless or cellular capabilities so that patient vital signs are only viewable in the physical presence of a patient.
"If you cannot disable the wireless capabilities, unplug the device and stop using it," the FDA said.
The FDA offered healthcare organizations using the monitors in their facilities similar recommendations. "If your patient monitor relies on remote monitoring features, unplug the device and stop using it. If your device does not rely on remote monitoring features, unplug the device's Ethernet cable and disable wireless capabilities," the FDA said. "If you cannot disable the wireless capabilities, then continuing to use the device will expose the device to the backdoor and possible continued patient data exfiltration."
CISA said the affected monitors are manufactured in China but deployed worldwide.
*Updated on Jan. 31 15:17 UTC to include additional CISA's details about the affected patient monitors' back door vulnerability.













