Cybercrime , Fraud Management & Cybercrime , Multi-factor & Risk-based Authentication
Recapping 2024's Top Attacks: Cybercrime, Espionage and More
Scattered Spider's Snowflake Hits, CrowdStrike Outage Implications and Beyond
What a year 2024 has been for cybersecurity - and its absence.
See Also: Mitigating Identity Risks, Lateral Movement and Privilege Escalation
With ransomware and other types of cybercrime on track to notch massive annual profits, and nation-state and cyber espionage operations appearing to remain both effective and nonstop, attackers' appetite for disruption, and the theft of data and cryptocurrency, feels like it's reached unprecedented levels.
Defenders have access to ever more sophisticated security tooling but these can create single points of failure, as seen with the CrowdStrike outage. Attackers continue to probe for fresh weaknesses in widely used open-source tools and security defenses, and to regularly compromise organizations that don't maintain the right patch cadence.
The stakes seem to keep getting higher and higher, driving both defenders to constantly test and deploy fresh strategies, and attackers to innovate.
Here are nine trends from the past 12 months.
Data Breaches Aren't in Decline
To anyone who hoped to see a decline in data breaches thanks to California's pioneering breach notification rule taking effect in 2003, or the General Data Protection Regulation rewriting Europe's privacy rules in 2018: Keep on dreaming. This year has seen its fair share of big, bad data breaches. Four million people's information got stolen through a breach of debt collector Financial Business and Consumer Solutions, while 560 million customers of Live Nation Entertainment's Ticketmaster saw their personal details get stolen.
Ransomware groups supplied extra chaos by breaching numerous health sector organizations, including UnitedHealth Group's Change Healthcare IT services unit, which attackers were able to penetrate due to a lack of robust controls such as multifactor authentication. The company said it expects to notify up to one-third of the American population - or more than 100 million people - that their protected health information was exposed, and to spend $2.9 billion on cleanup, including reportedly paying at least one ransom worth $22 million to attackers.
The Change breach highlighted that while Russia-based ransomware groups remain a scourge, researchers have been tracking the rise of Western affiliates, including groups spawned by "The Com" cybercrime community. Most individuals associated with these groups are native English speakers and seem to be very proficient in tricking help desks and other types of social engineering.
Cops Troll Extortionists
Not all is bad. Law enforcement continues to notch up impressive disruptions and arrests. This includes two individuals suspected of orchestrating the Snowflake and other attacks - U.S. citizen John Erin Binns and Canadian citizen Alexander Moucka, aka Connor Moucka - who were detained, respectively, in Turkey in May and Canada in November (see: Will Arrests Squash Scattered Spider's Cybercrime Assault?).
While permanently shuttering ransomware groups seems impossible, law enforcement gets credit for deploying fresh strategies. After infiltrating LockBit's data leak site, police replaced extortionists' shakedown posts with their own anti-LockBit messaging, revealing that they'd obtained a complete list of victim chats and decryption keys that the group's leadership had failed to protect, together with the handles for every one of the group's business partners (see: Europol Details Pursuit of LockBit Ransomware Affiliates).
Backdoors Serve Attackers Too
Irony alert: The Chinese nation-state attackers tracked as "Salt Typhoon" that penetrated at least nine U.S. telecommunications providers' networks, and more abroad, succeeded in part thanks to mandatory "lawful intercept" backdoors. Specifically, they were reportedly able to infiltrate infrastructure telecoms use to comply with court-authorized wiretaps of their subscribers' networking traffic.
Officials say ejecting attackers from the networks remains challenging. Guidance from U.S. cybersecurity officials for political figures and anyone else at risk from Beijing-backed cyber espionage campaigns suggests adopting encrypted communications and to use MFA wherever possible. In a stroke, this pro-crypto messaging has turned years of anti-encryption "going dark" rhetoric by political leaders and the FBI on its head (see: US CISA Endorses Encrypted Apps Amid Chinese Telecom Hack).
Edge Devices Under Attack
Entry points for telecom-targeting Chinese hackers reportedly included vulnerabilities in Cisco and other types of edge devices. Security experts say edge devices remain a top initial-access vector for criminal and nation-state hackers alike, given how many firewalls, email gateways and VPN gateways don't get patched in a timely manner.
Espionage groups in particular continue to find and exploit zero-day vulnerabilities in gear from the likes of Cisco, Fortinet, Palo Alto Networks and Sophos.
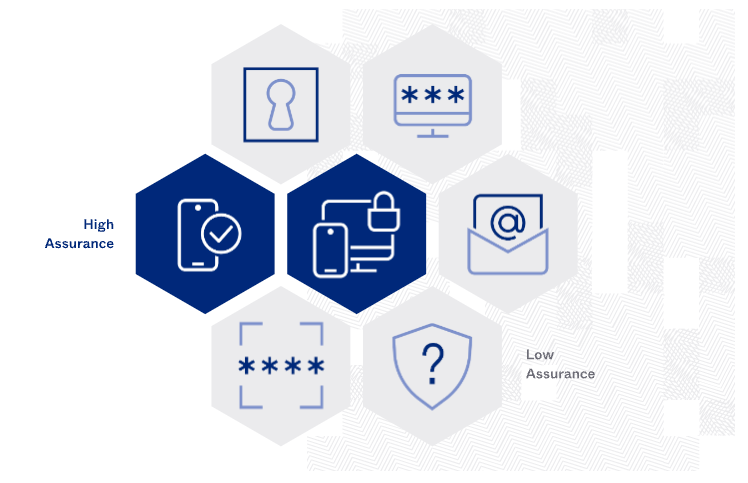
Missing MFA Bites
The previously mentioned Ticketmaster breach traced to a hacking group with ties to The Com - a community believed to have spawned groups researchers now track as Scattered Spider, 0ktapus, UNC3944 and others - that gained access to 165 organizations' data warehousing accounts with Bozeman, Montana-based Snowflake. Santander Bank, automotive parts supplier Advance Auto Parts, luxury retailer Neiman Marcus and Bausch Health were also among the small number of publicly named victims.
As with Change Healthcare, all of those victims had the same thing in common: their breached Snowflake accounts weren't being protected by optional multifactor authentication. While this feature is no silver bullet, it does stop outright many types of attacks, including when attackers have managed to phish, steal or otherwise obtain working username and password pairs for a service. Some Snowflake administrators did say that activating MFA for accounts could be challenging, and couldn't be enforced on a per-user basis (see: Multifactor Authentication Shouldn't Be Optional).
Facing serious fallout over the breach of its customers' accounts, Snowflake rethought its approach to MFA, making it active by default for all new accounts and promising to regularly nudge existing users who fail to activate it. How many other services will follow suit?
Uncertain Artificial Intelligence Future
As with so many super-promoted technologies, the nuances of what machine learning, AI and data analytics can truly do for good or bad continue to evolve. At the close of a year in which more than 2 billion people in more than 50 countries voted in major elections, one bright spot is that the effects of AI-driven election misinformation and disinformation appeared to be minimal. The same was not true for AI-driven fraud, thanks to such tools helping phishers and other social engineers craft much more convincing lures.
What about for defense? While practically every tool now claims to be powered by AI, experts point to its use case as augmentation not least in security operations centers and for expert use cases as a solid application. The jury remains out on some other use cases, such as Microsoft's beleaguered Windows Recall feature.
Single Points of Failure Remain
The massive, global outage in July triggered by a faulty CrowdStrike update could have been worse especially had it been caused by attackers with outsized, nefarious intentions. On the downside, seeing 8.5 million Windows hosts go down simultaneously is a reminder that such vulnerabilities remain open for targeting. Regulators are promising to take a much closer look at making the Windows ecosystem more resilient (see: After CrowdStrike Outage: Time to Rebuild Microsoft Windows?).
Open-Source Software at Risk
Attackers successfully subverted widely used XZ Utils and launched similar social engineering attacks against other popular open-source tools in April. That's a reminder that major open-source software projects that so often underpin critical infrastructure are maintained by just one or a handful of coders in their spare time, with minimal resources. Efforts are underway to help, including big tech firms pledging backing for open-source projects, and government moves to understand what OSS their agencies actually use, so they can better track and help secure it.
File-Transfer Software Under Fire Again
One repeat 2024 question has been: How long until the Clop ransomware group targets another type of widely used file-transfer software through a zero-day exploit? Following on from the group's third such attack in May 2023, the answer now appears to be about a year and a half, given the mass exploitation that came to light earlier this month, of Harmony, VLTrader and LexiCom MFT software built by Rockford, Illinois-based Cleo Communications. Clop, aka Cl0p, believed to be based in Russia, claims to now be extorting at least 66 organizations from which it stole data. Whether or not any victims already paid it hush money isn't clear. Stay tuned for more details in 2025.