Hunting CVE-2024-30051
Hunting CVE-2024-30051 Desktop Window Manager Privilege Escalation

Overview
CVE-2024-30051 is an out of bound write that has been identified in Desktop Window Manager that can be exploited to achieve privilege escalation to SYSTEM. The bug is a heap overflow in CCommandBuffer::Initialize of dwmcore.dll. This is similar to the Windows DWM Core Library Elevation of Privilege Vulnerability (CVE-2023-36033), which was a previously discovered zero-day exploited in the wild.
In early April 2024 researchers from various places identified active exploitation of this vulnerability by several threat actors. Kaspersky mentioned in an article that Qakbot has been using it recently, and identified an interesting article surrounding the technique.
“While searching for samples related to this exploit and attacks that used it, we found a curious document uploaded to VirusTotal on April 1, 2024. This document caught our attention because it had a rather descriptive file name, which indicated that it contained information about a vulnerability in Windows OS.”
After some digging around on VirusTotal we were able to find the mentioned article, and gain some insight into the exploitation of CVE-2024-30051.
Finding the Sample
Since it had been mentioned that Qakbot had been seen in association with this activity we started hunting through our partner’s platform, Google Mandiant Advantage, to find a sample that could be using this CVE. They had a single hit that appeared to have been uploaded to VirusTotal as well.
Using the hash we looked around and found it had also been uploaded to Hybrid-Analysis and Stairwell.
Detonation and Findings
We executed the sample in our Sandbox VM and immediately saw activity similar to what was reported in the pdf from VirusTotal. We can see dwm.exe activity in Process Monitor and our system shell was spawned.
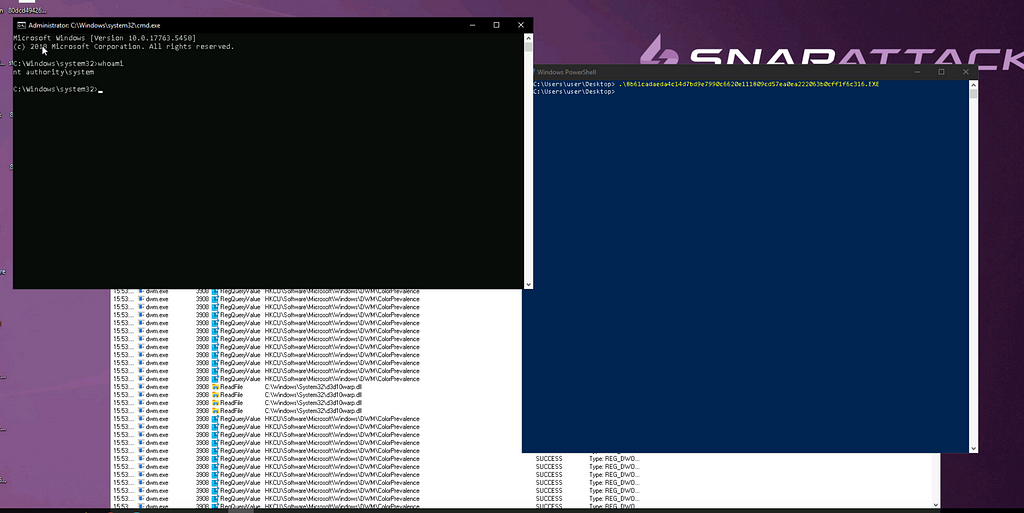
The exploit will cause a few things to happen on the victim machine that are fairly easy to detect. The first is the creation of some dlls that are loaded by the dwm.exe process outside of the System32 directory. In the case of our execution they were in C:\Users\Public\Documents.
EventCode: 7
Image: C:\Windows\System32\dwm.exe
ImageLoaded: C:\Users\Public\Documents\s1.dll
Signed: false
User: Window Manager\DWM-2vv
A few seconds into the exploit executing, a new dll will be created in the same location, but with the dwm.exe process as the creator.
ProcessName: dwm.exe
TargetFilename: C:\Users\Public\Documents\s3.dll
EventCode: 11
Image: C:\Windows\system32\dwm.exe
User: Window Manager\DWM-2
ProcessName: dwm.exe
ProcessPath: C:\Windows\system32\dwm.exe
EventDescription: FileCreate
FileName: s3.dll
FilePath: C:\Users\Public\Documents\s3.dll
From here a UAC consent window appeared for a moment before disappearing without any interaction. This is where several commands are executed with system context. The first starts a new command process with System permissions.
ParentProcessName: consent.exe
CommandLine: C:\Windows\system32\cmd.exe /c start cmd.exe
EventCode: 1
ProcessName: cmd.exe
UtcTime: 2024-05-16 16:00:18.061
Image: C:\Windows\System32\cmd.exe
ParentImage: C:\Windows\System32\consent.exe
ParentCommandLine: consent.exe 2792 288 0000016A8C9E1EF0
User: NT AUTHORITY\SYSTEM
IntegrityLevel: System
ProcessName: cmd.exe
ProcessPath: C:\Windows\System32\cmd.exe
ParentProcessPath: C:\Windows\System32\consent.exe
Action: allowed
Channel: Microsoft-Windows-Sysmon/Operational
CurrentDirectory: C:\Windows\system32\
Description: Windows Command Processor
ParentProcessPath: C:\Windows\System32\
ParentUser: NT AUTHORITY\SYSTEM
ProcessPath: C:\Windows\System32\
Product: Microsoft® Windows® Operating System
ParentProcess: consent.exe 2792 288 0000016A8C9E1EF0
ParentProcessExec: consent.exe
ParentProcessId: 788
ParentProcessName: consent.exe
The second terminates the dwm.exe process it used for exploitation.
ParentProcessName: consent.exe
CommandLine: C:\Windows\system32\cmd.exe /c taskkill /f /im dwm.exe
EventCode: 1
ProcessName: cmd.exe
UtcTime: 2024-05-16 16:00:18.204
Image: C:\Windows\System32\cmd.exe
ParentImage: C:\Windows\System32\consent.exe
ParentCommandLine: consent.exe 2792 288 0000016A8C9E1EF0
User: NT AUTHORITY\SYSTEM
IntegrityLevel: System
ProcessName: cmd.exe
ProcessPath: C:\Windows\System32\cmd.exe
ParentProcessPath: C:\Windows\System32\consent.exe
Action: allowed
Channel: Microsoft-Windows-Sysmon/Operational
CurrentDirectory: C:\Windows\system32\
Description: Windows Command Processor
ParentProcessPath: C:\Windows\System32\
ParentUser: NT AUTHORITY\SYSTEM
ProcessPath: C:\Windows\System32\
Product: Microsoft® Windows® Operating System
ParentProcess: consent.exe 2792 288 0000016A8C9E1EF0
ParentProcessExec: consent.exe
ParentProcessId: 788
ParentProcessName: consent.exe
Because it abuses the desktop window manager to create the cmd.exe process behind a consent window, we noticed the styling on the terminal window will sometimes be broken.
Looking at the process graph we can see the dwm.exe process is being spawned under winlogon process in order to have system permissions. We can also see the two cmd processes under consent.exe.
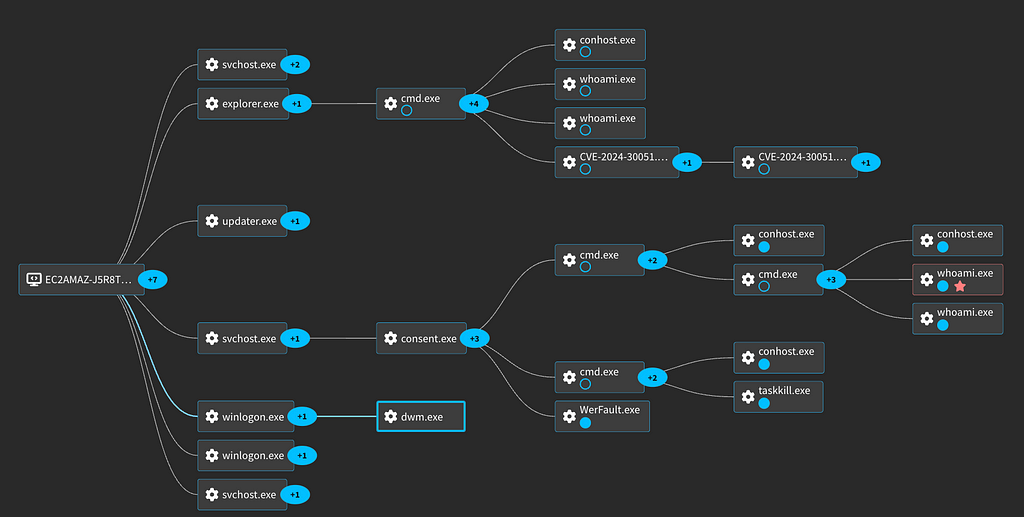
For more logs and details, we have captured this activity in our platform: CVE-2024-30051 Privilege Escalation via dwm
For Detections check out this Collection: CVE-2024-30051
MITRE
T1068: Exploitation for Privilege Escalation
Adversaries may exploit software vulnerabilities in an attempt to elevate privileges. Exploitation of a software vulnerability occurs when an adversary takes advantage of a programming error in a program, service, or within the operating system software or kernel itself to execute adversary-controlled code.
T1129: Remote Services: Shared Modules
Adversaries may execute malicious payloads via loading shared modules.
T1059: Command and Scripting Interpreter
Adversaries may abuse command and script interpreters to execute commands, scripts, or binaries.
T1548.002: Abuse Elevation Control Mechanism: Bypass User Account Control
Adversaries may bypass UAC mechanisms to elevate process privileges on system. Windows User Account Control (UAC) allows a program to elevate its privileges (tracked as integrity levels ranging from low to high) to perform a task under administrator-level permissions, possibly by prompting the user for confirmation.
T1218: System Binary Proxy Execution
Adversaries may bypass process and/or signature-based defenses by proxying execution of malicious content with signed, or otherwise trusted, binaries.
Conclusion
In summary, CVE-2024-30051 is a trivially exploited vulnerability to gain SYSTEM level permissions by abusing the Desktop Window Manager. It has been actively exploited by multiple threat actors over the last few months as part of post compromise activities. A patch has been released as part of May 2024’s Patch Tuesday to fix this vulnerability going forward.
SnapAttack is the threat hunting, detection engineering, and detection validation platform for proactive threat-informed defense. Register for a FREE community account to access the tons of content included in this blog post, as well as thousands of other community detections. Subscribers also get advanced features like a no-code detection builder, one-click deployments to leading SIEMs and EDRs like Chronicle, Sentinel, Splunk, CrowdStrike and SentinelOne, advanced threat profiles to prioritize relevant threats, and customized reports that track MITRE ATT&CK coverage and more! Check out snapattack.com to learn more.
Resources
- QakBot attacks with Windows zero-day (CVE-2024-30051)
- Mandiant Advantage
- Free Automated Malware Analysis Service – powered by Falcon Sandbox – Search results
- VirusTotal
- Stairwell
Hunting CVE-2024-30051 was originally published in SnapAttack on Medium, where people are continuing the conversation by highlighting and responding to this story.
*** This is a Security Bloggers Network syndicated blog from SnapAttack - Medium authored by Trenton Tait. Read the original post at: https://blog.snapattack.com/hunting-cve-2024-30051-8de021f0cf77?source=rss----3bac186d1947---4



