Research on Online Social Network Information Leakage-Tracking Algorithm Based on Deep Learning
- PMID: 35800694
- PMCID: PMC9256347
- DOI: 10.1155/2022/1926794
Research on Online Social Network Information Leakage-Tracking Algorithm Based on Deep Learning
Abstract
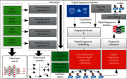
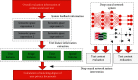
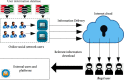
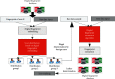
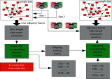
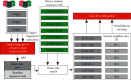
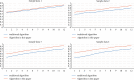
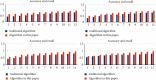
The rapid iteration of information technology makes the development of online social networks increasingly rapid, and its corresponding network scale is also increasingly large and complex. The corresponding algorithms to deal with social networks and their corresponding related problems are also increasing. The corresponding privacy protection algorithms such as encryption algorithm, access control strategy algorithm, and differential privacy protection algorithm have been studied and analyzed, but these algorithms do not completely solve the problem of privacy disclosure. Based on this, this article first searches and accurately filters the relevant information and content of online social networks based on the deep convolution neural network algorithm, so as to realize the perception and protection of users' safe content. For the corresponding graphics and data, this article introduces the compressed sensing technology to randomly disturb the corresponding graphics and data. At the level of tracking network information leakage algorithm, this article proposes a network information leakage-tracking algorithm based on digital fingerprint, which mainly uses relevant plug-ins to realize the unique identification processing of users, uses the uniqueness of digital fingerprint to realize the tracking processing of leakers, and formulates the corresponding coding scheme based on the social network topology, and at the same time, the network information leakage-tracking algorithm proposed in this article also has high efficiency in the corresponding digital coding efficiency and scalability. In order to verify the advantages of the online social network information leakage-tracking algorithm based on deep learning, this article compares it with the traditional algorithm. In the experimental part, this article mainly compares the accuracy index, recall index, and performance index. At the corresponding accuracy index level, it can be seen that the maximum improvement of the algorithm proposed in this article is about 10% compared with the traditional algorithm. At the corresponding recall index level, the proposed algorithm is about 5-8% higher than the traditional algorithm. Corresponding to the overall performance index, it improves the performance by about 50% compared with the traditional algorithm. The comparison results show that the proposed algorithm has higher accuracy and the corresponding source tracking is more accurate.
Copyright © 2022 Shuhe Han.
Conflict of interest statement
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this article.
Figures
Similar articles
-
Research on Information Leakage Tracking Algorithms in Online Social Networks.Comput Intell Neurosci. 2022 Oct 4;2022:5634385. doi: 10.1155/2022/5634385. eCollection 2022. Comput Intell Neurosci. 2022. PMID: 36238673 Free PMC article.
-
Privacy Protection and Intrusion Detection System of Wireless Sensor Network Based on Artificial Neural Network.Comput Intell Neurosci. 2022 Jun 22;2022:1795454. doi: 10.1155/2022/1795454. eCollection 2022. Comput Intell Neurosci. 2022. PMID: 35785102 Free PMC article.
-
Optimization of a Deep Learning Algorithm for Security Protection of Big Data from Video Images.Comput Intell Neurosci. 2022 Mar 8;2022:3394475. doi: 10.1155/2022/3394475. eCollection 2022. Comput Intell Neurosci. 2022. Retraction in: Comput Intell Neurosci. 2023 Aug 2;2023:9762462. doi: 10.1155/2023/9762462 PMID: 35300398 Free PMC article. Retracted.
-
[Review of research on detection and tracking of minimally invasive surgical tools based on deep learning].Sheng Wu Yi Xue Gong Cheng Xue Za Zhi. 2019 Oct 25;36(5):870-878. doi: 10.7507/1001-5515.201904061. Sheng Wu Yi Xue Gong Cheng Xue Za Zhi. 2019. PMID: 31631638 Free PMC article. Review. Chinese.
-
Analysis of Application Examples of Differential Privacy in Deep Learning.Comput Intell Neurosci. 2021 Oct 26;2021:4244040. doi: 10.1155/2021/4244040. eCollection 2021. Comput Intell Neurosci. 2021. PMID: 34745246 Free PMC article. Review.
References
-
- Liu W., Zhu M., Dai C. Classification of large-scale stellar spectra based on deep convolutional neural network. Monthly Notices of the Royal Astronomical Society . 2019;483(3):4774–4783. doi: 10.1093/mnras/sty3020. - DOI
-
- Wang Z., Ma H., Chen H. Performance degradation assessment of rolling bearing based on convolutional neural network and deep long-short term memory network. International Journal of Production Research . 2020;58(4):113–123. doi: 10.1080/00207543.2019.1636325. - DOI
-
- Xiong Y., Chen Y., Chen C. An odor recognition algorithm of electronic noses based on convolutional spiking neural network for spoiled food identification. Journal of the Electrochemical Society . 2021;168(7):077519–007523. doi: 10.1149/1945-7111/ac1699. - DOI
MeSH terms
LinkOut - more resources
Full Text Sources

