,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,
,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,
,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,
,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,
,,,,,,,,,,,,,,,,,,,,,,,,,..,,.,,,,.,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,
,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,.,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,
,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,...,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,*%%#****/(/###((((*(***///*,,,,,,
,,,,,.,,,,,,,,,,,,,,,,,,,,,,,,,.........,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,/%%%%%%%%#%%%%##%#(%%###((/#(#(,,,,
,,,,,,,,,,,,,,,,,,,,,,,,,,,,.............,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,*%%%#%%%%#%%(#%%&###(#(((((###*,,,
,,,,,,,,,,,,,,,,,,,,,,,,,,,,,...............,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,**##%%##%#%%#%#%%#%%%/(((((((/(((#/*,,
.,,.,,,,,,,,,,,,,,,,,,,,,,,,......................,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,%&&%%#%&@&%(%%#%####%@%/#/(#(((%(*,,
..,.,,,,,,,,,,,,,,,,,,,,,,...........................,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,&%((%%@@%%######(%@@%#(((((((/,,,,,
....,,,,,,,,,,,,,,,,,,,,,,.............................,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,%%(#&%%%##&%&&%%#(/((##(/(/(((/,,,,
.....,.,,,,,,,,,,,,,,,,,,...............................,,,,,,,,,,,,,,,,,,,,,,,,,,,,*/##%&%%%&&%%%#((((#/#(#////%,,,,,,,
..,,,,,,,,,,,,,,,,,,,,,,..................................,,,,,,,,,,,..,..............**(/(##%%(%###(*(((((/,,..,(,,,,,,
....,,,,,,,,,,,,,,,,,,,,,...,.........................................................**//**//////****,.*..,......,,,,,,
.......,,,,,,,,,,,,,,,,,,,,,,,........................................................**/*//*///////*,.,......,.. ,,,...
..........,,,,,,,,,,,,,,,,,,,,........................................................(/**//////((///////*,**.. ......
.........,.,,,,,,,,,,.,.,,.,,.........................................................*/*///((((//(((//*/*,,. . .....
.........,,,,,,,,,,,,.,,,,,...........................................................((**//*/******/*****.,... ,...
.........,,,,,,,,,,,,,,,,................................................,,,..........#(******,,*,,,.,,**,.... .,..,
,.,,,,,,,,,,,,,,,,,,,,,,.....,......,........,,,,................,...,,,,,,,,,,,,,,..,%#//*,,,.,,,.,,*,..... .,,,,,
,,,,,,,,,,,,,,,,,,,,,,,..............,,,,,,,,,,,,,,..........,....,,,,,,,,,,,,,,,,,,.#%%/(,*.,,., ., ...... ,,,,,
,,,,,,,,,,,,,,,,,,,,,.......,,,,........,,,,,,,,,..................,,,,,,,,,,,,,,,,,,#%%/,*,,*.*..*... . . ,,,,,,
,,,,,,,,,,,,,,,...........,,,,,...........,,,,,,,......................,,,,,,,,,,,..#%%&((.,*..,,.,.. . .,,,,,,
,,,,,,,,,,................,,,................,..............................,,,....%##%/,/*.* ,,,*.... .......
..,.,,,,,..................,.,,,.................................................(%#%%%&(%*/,*.,* .... .......
.............................,,.............................................../%%%%%&%%(##/*//.,,.. . .........
...........................................................................(%%%%#%&%&&%#%(#**, ,,.*.. ........
.......................................................................,/#%%&%%%%&&&&%%(/*# ***,,.. ...........
....................................................................*#%%%%%&%%%%&%%%###(*(*/*..,.. . ............
.....,,,,..........,,....,..,,................................,(###%&&&&&&%%&%&&%%#%%%(%((#/,.,*,.. . .........
..,,,,,,,,,.....,,,,**./(#((//**,.....................**(##%%%%&&%%&&&&&&&&%%%%#%%&%#%%(##(#*,. . ......,,,,.
.,,,,,,,,,....*(##%####%%%#%%%%#%##%#(*........,(######%%%%%%%##&%%&&&&&@@%&%%%%%%###%#((/(,... .. .............
.,..........*/%%###%%#%%%%#%%##%%%%%%%#%##%##%%%##%%&%%%%%%&&%%%%&&%%%%%&&%&%%%%%#%%#%#%#%##(*, .. ............
.........,#%%%%%##%%#%########%%%##%%%%%%%#%%%%%%%%%%%&%%%&&%%&%%%&&&&&&&&%%&&%&###%#(%%(#**. . ...............
,,,,,,,*#%%%%%%%%%%%####%%%%#%%%%%%%%#%%#%%%%%#&%%%%%%%%%#%%&%%%%%&%&&&@&@&%&&%%&####%%(%%(,. . .................
**,,,,*##%%%%%%%%###%%#%%%%%####%#%%#%%#%%%%%%%%%%%%%%%#%%%#%%&%&%%&%%##%(((%%%#(####(##(*. . .,..,,,,,,,...........
**,,*####%&%%%%#(###%%%%%%###%%###%%%%%%%%%%%%%%%%%&%%%%%%&%%%%%%%%&&&%&/*,**/((%###((#%#%/, . ,,,,,,,..............
**(##%%%%%%%%%%%%#%%#%#########%%%%##%%%%%%%%%%%%%%#%%#%%%%%%%%&&%%%%##/,*,****/*###(#(%/##((. ,***********///***...
/#######%%%%#%%%&&%%##%####%#%##%%%#%%#%%%%%#&%%%%%&%%#&%%%%&&%%####/*/**,/****/((##((##(#(. . **,*****************,,,**
/$###%%%%%%%%%&&%&&&&%%##%%#%%%%%%%%%%%%%%%%%%&%%&&%&&%%%%&%%#%&%%((*,,,,,**//////(####(/##(* ...,,,,,**************,,,,
/##%&&%&&%%%&%%%%#%&%%&&%%%%%%%%#%#%#/****///(((###(###(#(#(*/,*,,,,****/***//((((((##((//(/* *,,,. .,,.. .,**,...
#%%%%%%&&&&@&&&&%%%%&%%%&&%&%%#%##((*/*/****,**//*****,*,*,,,,.*,*,,,/(////(#((#(*,,(((/(///,..,. .. .,. ....,****,,.
/#%%%%%%%&&&@@&&%%%%%%%%%%%%(((((*/*/*/***/**,*,**,*,,,,*.,*,,,**,**/(#(##(((*,. .*(///*/,., .,,**,,. . ,*///*,,,,.
//%&%%%&&&@@@@&&%&%#(#%%%%%%%(////***/(**/**/*****/*,*,**/***///**((//./*,,*,****,**.((/(/**,,,. ,,*,*,** .,,,,..,...
*/#%%%%%&&&&@@@@@@&&&%#######%###((//**/(((((///*//**////////*///**,,,*(%(*(**,*(.*(//(//%((#/*,*/*,,.....*.,.,**,//.
*/*/%/***/**/***/****((///,,*,.####//*/*,,,//**,//,(*/**,,**//****,,,. ..,*,***,*,,*,,**/ ,*////*,..,*,,***,,,*/*,******
*******,*(////*,,*(/***,,************/**/**//***////***/**,**//****,,.,,,********/*,,,*,,***,,*****,,,.******,**,**,,.,*
*********/(((//***/********//////**//********,,**///******/////*******/*//*********************///**,*/***,****/***/****
******///****/////////****,******************************///////////////////(//*******,******,,****,,*******,,//////////
*****/*********///**///**,,,,**************/*//****//*////////////////////////*********///***,,,*///******//////////////
//***/*****************//****************//////////////////////**********/////********////******/////***//*****/////////
//*/////**************////******//******////////******/*//////////********************//*****/////////////**********////
******//**************/////******/*****/////******///////////////***/**////**********/////////////////////////****//////
********************////******/*******//////*****////////////////***///////////////////////////////******///////////////
******************///////*************///////***//////////////////****/////////////******//////////******///////*/**/***
//**************//////////***/***************//////*************////*////****///////////////////////////////********////
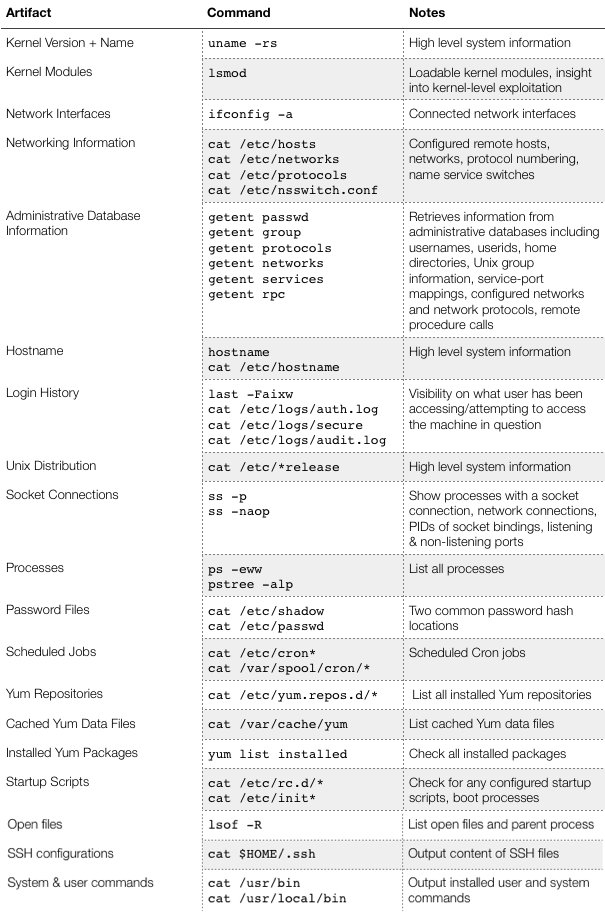
In a 2017, the average time an attacker has access to a compromised machine to when they are discovered is 101 days. While a great improvement from a dwell time of 400 days in 2011, 101 days is not the desirable zero, demonstrating a need for a reliable method of assessing the integrity of managed machines. The purpose of Unix Security Weasel is to perform artifact collection on Unix systems, allowing a forensic security analysts to review the artifacts and determine the integrity of the system. The tool is designed to be used in the intrusion detection or response process, where beyond assessing the integrity of a system, it can give insight into the scope or method of exploitation.
Artifact collection depends on two important factors, the complete collection of all files of interest and the assertion that these files are has its integrity preserved. By understanding the commands built into the COMMAND dictionary structure, an analyst can understand what artifacts are being retrieved and their importance in identifying a compromised machine, as well as be assured of their integrity given the collection method.
- Unix Artifact Weasel requires superuser privileges, so run with
sudo python3 UnixForensicWeasel/run.py - Alternatively, users can write a shell script with the following content and use it as the executable:
#!/bin/bash # Can be a path to a python3 virtual environment (recommended) or # path to base interpreter PATH_TO_PYTHON_ENV=“/Users/JDoe/Documents/UnixArtifactWeasel/venv/bin/python3" PATH_TO_PYTHON_PROG=“/Users/JDoe/Documents/UnixArtifactWeasel/run.py” sudo $PATH_TO_PYTHON_ENV $PATH_TO_PYTHON_PROG - Without superuser privileges, the program will exit with an error without performing any artifact collection
- Unix Forensic Weasel creates a log folder in
/var/log/unixforensicweasel, storing a log file per execution in the format{yyyy}-{mm}-{dd}_{hour}:{min}:{sec}.log - There are four fields in each log entry, SECTION, COMMAND, ERROR, and OUTPUT
- SECTION notes the current section of artifacts Unix Artifact Weasel is collecting, such as ‘login history’ or ‘user commands’
- COMMAND notes the command executed in order to obtain the current artifact being collected
- ERROR stores a boolean, TRUE or FALSE, about whether the subprocess returned an error during command execution
- OUTPUT notes the output returned by the subprocess that executed the given command.
- In the case of an error, OUTPUT will note the error message